Ohh My God, An Other Threat Alert
Are you aware about the latest OpenSSL threat alert?
If not, here is some information and how to check if your computer is affected or not
On November, 1st 2022 the OpenSSL Project disclosed CVE-2022-3602 and CVE-2022-3786 – critical severity vulnerabilities present in OpenSSL 3.0.x.
Actions required:
Identify if OpenSSL 3.X is running on your environment. If you would like to make your life easy, use this script which is available in githug
1. Download and unzip the script from https://github.com/MalwareTech/SpookySSLTools
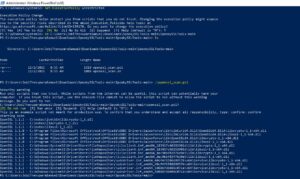
Scanning Windows Systems
-From the start menu, locate PowerShell, right click the icon, and select “Run as Administrator”
-Type the command Set-ExecutionPolicy unrestricted and press enter
-Navigate to the directory that you have downloaded openssl_scan.ps1 to
-choose “.\openssl_scan.ps1” and enter
-After few minutes you’ll get the results. You will be presented with the results of any version(s) of vulnerable OpenSSL running on the machine. Take note of the results.
If your machine have OpenSSL 3.X which is vulnerable version, then OpenSSL need to be upgraded to version 3.0.7
Scanning Linux Systems:
-download openssl_scan.sh from https://github.com/MalwareTech/SpookySSLTools
-Open a bash terminal and navigate to the directory that you have downloaded openssl_scan.sh to
-Type the command chmod +x ./openssl_scan.sh and press enter to make the script executable
-Type the command ./openssl_scan.sh and press enter to run the script
-You will be asked to confirm
-Once the script has completed check the result, if your system have OpenSSL 3.x then you need to be upgraded to version 3.0.7
Download the fix directly from vendor site or from here https://github.com/NCSC-NL/OpenSSL-2022/blob/main/software/README.md
Reference:
https://github.com/NCSC-NL/OpenSSL-2022/blob/main/software/README.md
https://github.com/MalwareTech/SpookySSLTools