So you want to know whether your system is affected by CVE-2022-0778 OpenSSL Vulnerability?
Using few commands, you can check if you are affected or not.
Before going to the command, do you know what is OpenSSL or why we use openssl?
OpenSSL is a software library for applications that secure communications over computer networks
Openssl- Real world scenario
Let’s take bank as an example.
If you do any banking you maybe asked to sign a contract right?
When bank issue a contract, the terms and conditions mentioned in that document.
Now Imagine some one send you a contract, you sign the contract but how do you know you’re signing the correct contract? or a third person is not modifying the contract or altering the terms and conditions?
Do you see why this is important?
Both of you should make sure the contract you’re signing is what you suppose to sign.
In the digital word, in order to ensure software has not been tampered, a digital finger print is used.
That digital finger print can be used to make sure files or software code’s are original.
Openssl can be used to create digital finger print.
Openssl support several algorithms for creating this fingerprint for example MD2, MD4,MD5,SHA,SHA1 etc.
You can go to openssl help to see all supported algorithms. Each algorithm provides different level of security
Now imagine you have an important file called contract and you want to make sure nobody is modifying. How will you do that?
With the help of a simple openssl command you can achieve this if your system installed with OpenSSL
Openssl dgst -md5 /home/confidential/contract
The above command will create an md5 hash algorithm and you can use that hash to verify its originality.
If you need to check if the file was modified, you can compare the current fingerprint with the fingerprint calculated above. Example contract file
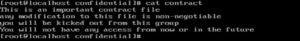
Contract file hash

Contract file modified
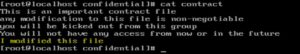
Hash changed
This is one of the use case of OpenSSL but OpenSSL can be used for other reasons as well
National vulnerability database recently found a bug in some of the OpenSSL version which give an unauthorized user access to your system so it is important you check your OpenSSL version and make sure you’re not running any compromised OpenSSL version
Do you know what versions installed on your systems?
Compromised OpenSSL versions
OpenSSL 3.0.0 to 3.0.1 (Fixed in OpenSSL 3.0.2)
OpenSSL 1.1.1 to 1.1.1m (Fixed in OpenSSL 1.1.1n)
OpenSSL 1.0.2 to 1.0.2zc (Fixed in OpenSSL 1.0.2zd)
How to check OpenSSL version on ESXi or vCenter ?
Login (root) to your host and type openssl version -a
If you got other systems like linux or windows. Take a command prompt and type openssl help
Who is more vulnerable to this bug?
If your systems is internet facing, you’re more vulnerable.
So make sure internet facing system’s are updated as early as possible to fix this issue
Non-vulnerable OpenSSL versions
(fact checked on 23.3.2022)
OpenSSL 1.0.2zd and above
Do you have any question related to this topic?
Share